Key Reasons for Encrypting Communications

Data Confidentiality
In an increasingly interconnected world, safeguarding sensitive information is critical for businesses, governments, and individuals alike. Encryption ensures that confidential data remains private by converting it into unreadable code that only authorized users can decipher. Whether it's personal data, corporate secrets, or government intelligence, encryption acts as a powerful barrier against unauthorized access, preventing hackers, criminals, and even insiders from compromising this crucial information. As communication channels expand across email, messaging, and cloud storage, encryption serves as the gatekeeper, ensuring that sensitive data is only seen by those who are authorized to access it.
Protection Against Cyber Threats
Cyberattacks are becoming more sophisticated and diverse, with attackers using advanced techniques such as AI-powered threats and deepfake technologies to carry out fraud and identity theft. These evolving threats put businesses, governments, and individuals at risk of data breaches, ransomware attacks, and exposure of critical information. Encryption is a fundamental line of defense against these risks, ensuring that even if data is intercepted or stolen, it remains unreadable and useless to unauthorized parties. With encryption in place, organizations are better protected from man-in-the-middle attacks, malware infections, and unauthorized surveillance, providing an additional layer of security in an age where cyber threats are omnipresent.
Defense Against Cyberespionage & Safeguarding National Security
Nation-state actors, corporate spies, and cybercriminals constantly target sensitive government and corporate communications. Encryption is a critical defense, protecting national security, government intelligence, and business strategies from espionage and cyber threats. By securing confidential data and communication channels, encryption ensures that foreign adversaries and malicious actors cannot compromise sovereignty or gain unauthorized access to classified information. In an era of rising cyber warfare and industrial espionage, encryption helps maintain control over critical data, safeguarding a nation's resilience and corporate competitiveness.
Mitigating Social Engineering Risks
Phishing, impersonation, and other forms of social engineering continue to be some of the most effective tactics used by cybercriminals to gain unauthorized access to sensitive data. These attacks often rely on tricking individuals into disclosing confidential information, such as login credentials or financial data. However, encrypted data adds a significant layer of protection, as stolen data remains unreadable and unusable to the attacker, even if they manage to access it. With encryption in place, organizations can mitigate the impact of these increasingly common threats, ensuring that malicious actors cannot exploit human error to compromise critical information.
Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks occur when attackers intercept and potentially alter communication between two parties without their knowledge. This type of attack is especially dangerous in situations involving financial transactions, confidential communications, or personal information. Authentication, especially during key exchange, plays a key role in mitigating MITM attacks by ensuring that intercepted messages remain secure, preventing attackers from gaining access to sensitive data. Whether it's email communication or online banking transactions, encryption secures the integrity and confidentiality of information in transit.
Compliance with Regulations
As data privacy and protection laws become more stringent worldwide, encryption is no longer just a best practice but a regulatory requirement. Regulations like GDPR, the EU's General Data Protection Regulation, and NIS2 in Europe, as well as laws like HIPAA and PCI-DSS, mandate encryption to protect sensitive data. Failure to comply with these laws can lead to heavy fines, legal penalties, and irreparable damage to an organization’s reputation. Encrypting communication ensures that businesses and governments meet legal requirements, reduce their exposure to compliance risks, and protect the personal and financial data of their customers, employees, and citizens.
Preventing Data Breaches and Insider Threats
Even the most secure systems are vulnerable to human error and insider threats, making data breaches a persistent risk. Insider threats, whether from malicious employees or those with access due to negligence, are among the most difficult security risks to manage. While traditional cybersecurity measures protect against external threats, encryption, E2E encryption in particular, offers a safeguard even when data is accessed by individuals within the organization. With encryption, sensitive data is protected from unauthorized access by internal actors, minimizing the risk of data theft, misuse, or accidental exposure. By ensuring that even insiders cannot read or alter sensitive information without proper authorization, encryption serves as an essential defense against one of the most insidious forms of security breach.
Securing Remote Work & Mobility
As remote work becomes more prevalent, ensuring secure communication over potentially insecure networks, such as public Wi-Fi or mobile hotspots, becomes crucial. Encryption plays a vital role in securing communications between remote workers and their organizations, preventing unauthorized access and data interception while ensuring that confidential information remains protected. Whether it's a government official sending a secure report from a café or a corporate employee working from home, encryption ensures that their communications remain private, no matter where they are or what network they use.
Ensuring Trust & Business Continuity
A data breach or security compromise can have devastating effects on an organization, not only leading to financial losses but also causing significant damage to its reputation. Encryption plays a crucial role in protecting sensitive data and preserving trust with customers, employees, and business partners. By safeguarding communications and data, encryption helps ensure business continuity, reducing the risk of costly disruptions and protecting the organization’s reputation. With strong encryption practices in place, businesses can demonstrate their commitment to security, building trust with stakeholders and maintaining operations even in the face of potential threats.
Futureproofing Against AI & Quantum Computing Threats
The rapid development of quantum computing presents significant challenges for traditional asymmetric-key cryptographic methods. As quantum computers hold the potential to crack widely used asymmetric-key cryptographic algorithms, organizations must prepare by adopting more advanced encryption solutions. Quantum-safe encryption is emerging as a key solution to protect against the growing threat posed by quantum computing, ensuring that communications remain secure in the face of future technological advancements. By investing in next-generation encryption now, governments and organizations can futureproof their data and communications, staying ahead of these emerging threats and ensuring long-term security.
Why Encrypted Communication Matters
In today’s fast-paced, digital-first world, sensitive data is constantly being transmitted across networks. Whether it’s government intelligence, personal data, or financial transactions, the volume and variety of information being exchanged is vast. This creates an increasing need for robust encryption mechanisms to safeguard this valuable information from a growing array of threats, including cybercriminals, hackers, and even surveillance programs by nation-states.
- The Rising Threat of Cyberattacks
Cyberattacks are escalating at an alarming rate, with data breaches rising by 30% in recent years alone. These attacks can have devastating consequences for businesses, governments, and individuals. For governments and organizations, the financial toll of a data breach can easily exceed millions of dollars, not just in terms of immediate recovery costs but also due to long-term reputational damage, regulatory fines, and lost business. According to IBM’s Cost of a Data Breach Report, the average cost of a data breach was $4.45 million in 2023, marking a 15% increase over the past three years. Encryption directly mitigates this risk by transforming sensitive data into unreadable code, ensuring that even if data is intercepted, it cannot be accessed or used by malicious actors. By implementing encryption, organizations significantly reduce their exposure to these costly security breaches.
- Legal Compliance and the Need for Encryption
Regulations like the General Data Protection Regulation (GDPR) in the EU, Health Insurance Portability and Accountability Act (HIPAA) in the U.S., and Payment Card Industry Data Security Standard (PCI-DSS) all mandate the use of encryption to protect sensitive data. Non-compliance with these regulations can result in hefty penalties. For example, a company that violates GDPR may face fines up to 4% of their global turnover or €20 million (whichever is greater). Encryption helps organizations meet these compliance requirements, ensuring that sensitive personal data is protected from unauthorized access and reducing the likelihood of severe penalties due to non-compliance.
- Privacy Protection and the Role of Encryption
Privacy is at the forefront of global concerns, especially when it comes to personal data like health records, financial details, and communication. With increased digital interactions, the amount of personal data being collected, stored, and shared is skyrocketing. Encryption is crucial in protecting this data from unauthorized access, whether that’s from cybercriminals attempting to steal identities, hackers looking to profit from personal information, or governments conducting surveillance. By employing encryption, individuals and organizations can rest assured that their sensitive information, whether communicated through emails, messaging apps, or cloud services, is kept private and secure.
With the implementation of encryption, businesses and governments also protect their customers’ trust. Today, consumers expect their data to be protected with the highest standards of security, and failure to safeguard that data can lead to a loss of business, not to mention irreparable reputational damage.

Chapter 2: Importance of Encrypted Communication in Various Sectors
From government agencies and healthcare providers to financial institutions and enterprises, secure communication is essential to prevent cyber threats, comply with regulations, and maintain public trust.
Each sector faces unique challenges, but the underlying need for encryption remains the same: to ensure confidentiality, integrity, and security. Whether protecting national intelligence, securing financial transactions, or safeguarding patient records, encryption acts as the backbone of data security strategies.

Encrypted Communication in Government Agencies
Government agencies manage vast amounts of classified and sensitive data, making them prime targets for cyber espionage, nation-state attacks, and internal leaks. Encryption is a fundamental layer of security that protects national security interests, diplomatic communications, and citizen data from unauthorized access.
Why Encryption is Essential for Governments
- Safeguarding National Security & Intelligence - Government entities deal with highly confidential data, including military intelligence, law enforcement investigations, and cybersecurity strategies. Encrypted communication ensures that classified information remains inaccessible to adversaries, reducing the risk of intelligence leaks.
- Preventing Cyber Espionage & Foreign Interference - Nation-state actors often target government agencies to intercept confidential communications and manipulate data. Encryption shields sensitive information from unauthorized surveillance, protecting the integrity of diplomatic negotiations, defense strategies, and geopolitical operations.
- Securing Citizen Data & Public Services - Government agencies store and process vast amounts of citizen data, from social security numbers to tax records and healthcare information. Encrypted communication prevents data breaches, ensuring that personal information remains private and protected.
- Compliance with National Security Regulations - Many governments mandate the use of encryption to protect critical infrastructure and sensitive information. Regulations such as the National Institute of Standards and Technology (NIST) encryption standards and the European Union’s General Data Protection Regulation (GDPR) enforce strict encryption guidelines for government entities.
- Mitigating Insider Threats & Unauthorized Access - Government employees and contractors often handle sensitive information. Encryption ensures that even if credentials are compromised or an insider attempts unauthorized access, classified data remains secure and unreadable.
As cyber threats against government entities continue to evolve, encryption remains a cornerstone of national security. Investing in advanced encryption technologies, including quantum-safe encryption and zero-trust security models, will be crucial for future-proofing government communications.
Encrypted Communication in Military Operations
For military operations, encryption is not just about protecting data but ensuring mission success, operational security, and the safety of personnel. Military forces rely on encrypted communication to secure battlefield coordination, intelligence sharing, and command directives, preventing adversaries from intercepting, altering, or exploiting mission-critical information.
Why Encryption is Essential in Military Operations
- Securing Real-Time Battlefield Communications - Military units operate in high-risk environments where instant and secure communication between soldiers, commanders, and intelligence teams is vital. Encryption ensures that real-time battlefield communications remain protected from enemy surveillance and cyber interference.
- Preventing Enemy Interception & Electronic Warfare - Modern adversaries deploy advanced cyber capabilities, including signal jamming, hacking, and electronic warfare tactics, to intercept military transmissions. Strong encryption protocols prevent hostile forces from deciphering intercepted messages or launching cyberattacks to manipulate mission data.
- Protecting Military Intelligence & Strategic Planning - Military intelligence operations involve gathering and transmitting sensitive data about enemy movements, geopolitical threats, and classified mission details. Encryption ensures that intelligence reports, drone surveillance data, and reconnaissance findings remain protected from unauthorized access.
- Enhancing Secure Communications Across Forces & Allies - Global military alliances, such as NATO, require encrypted communication channels to share intelligence and coordinate joint operations securely. Standardized encryption protocols allow allied forces to collaborate without the risk of data breaches.
- Ensuring Command & Control Resilience in Cyber Warfare - As cyber warfare becomes a major battlefield, adversaries attempt to disrupt military command-and-control systems through hacking, malware, or denial-of-service (DoS) attacks. Encryption strengthens military networks against cyber threats, ensuring that mission directives remain protected and unaltered.
Encrypted Communication in Energy and Utilities
The energy and utilities sector is a critical infrastructure that powers economies, supports national security, and ensures the smooth functioning of essential services. Given its importance, this sector has become a prime target for cyberattacks, ranging from ransomware incidents to state-sponsored espionage. Encryption plays a pivotal role in protecting sensitive data, securing industrial control systems (ICS), and ensuring the resilience of power grids and utility services against cyber threats.
Why Encryption is Essential in Energy and Utilities
- Protecting Critical Infrastructure from Cyberattacks - Power grids, oil refineries, water treatment plants, and gas pipelines are increasingly digitized and connected, making them vulnerable to cyberattacks. Encryption safeguards communication between control systems, preventing malicious actors from disrupting operations or causing blackouts.
- Securing Industrial Control Systems (ICS) & SCADA Networks - Supervisory Control and Data Acquisition (SCADA) systems and Industrial Control Systems (ICS) control the flow of electricity, water, and gas. Encryption ensures that commands sent to these systems remain secure, preventing cybercriminals from manipulating infrastructure settings.
- Preventing Espionage & Data Breaches in Energy Research - The energy sector handles sensitive data on power generation, renewable energy technologies, and nuclear research. Cyber espionage campaigns target this data to steal intellectual property and disrupt energy security. Encryption prevents unauthorized access to confidential research and innovation.
- Ensuring Secure Communication Between Remote Facilities - Energy companies operate facilities in remote locations, including offshore oil rigs, solar farms, and wind energy sites. Secure communication between headquarters and these sites is essential to maintain safe operations. Encryption ensures that remote monitoring, real-time sensor data, and maintenance logs remain confidential and tamper-proof.
- Regulatory Compliance & National Security Requirements - Governments worldwide impose strict cybersecurity regulations on the energy sector to prevent disruptions and safeguard national security. Encryption is a key requirement in compliance frameworks like:
- NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) for securing power grid communications.
- EU NIS2 Directive for strengthening cybersecurity across essential services, including energy and utilities.
- ISO 27019 for information security in industrial automation and control systems.
Encrypted Communication in Financial Services
The financial sector is one of the most heavily targeted industries for cyberattacks due to the vast amounts of sensitive data it handles daily. From banking transactions to investment portfolios and customer financial records, encryption is a fundamental security measure that protects against fraud, cyber threats, and regulatory non-compliance. Without robust encryption, financial institutions risk data breaches, financial losses, and reputational damage.
Why Encryption is Essential in Financial Services
- Securing Digital Transactions & Preventing Fraud - With the rise of digital banking, mobile payments, and online financial services, secure communication is critical to preventing unauthorized access and fraudulent transactions. Encryption ensures that financial data remains confidential and cannot be intercepted during transmission.
- Protecting Customer Data & Preventing Identity Theft - Banks and financial firms store vast amounts of personally identifiable information (PII), including Social Security numbers, account details, and credit history. Encryption ensures that even if a system is compromised, sensitive customer data remains unreadable to cybercriminals.
- Preventing Insider Threats & Unauthorized Access - Financial institutions often face risks from internal employees or contractors who may misuse their access to sensitive financial information. Encryption ensures that even those with system access cannot view or manipulate data without proper authorization.
- Compliance with Financial Regulations & Data Protection Laws - Regulatory bodies worldwide mandate encryption as a requirement for financial services to ensure data security and consumer protection. Non-compliance can result in hefty fines and legal consequences. Key regulations include:
- PCI-DSS (Payment Card Industry Data Security Standard) - Requires encryption of payment data during transmission and storage.
- GDPR (General Data Protection Regulation - EU) - Mandates encryption for customer data to protect against breaches.
- SOX (Sarbanes-Oxley Act - US) - Requires secure handling of financial records and communications.
- NYDFS Cybersecurity Regulation - Requires encryption for financial institutions operating in New York.
- Safeguarding Cross-Border Transactions & Blockchain Security - Global financial transactions require secure communication channels, especially with the increasing adoption of blockchain-based payments and cryptocurrencies. Encryption is vital to ensuring the integrity of transactions and preventing unauthorized tampering.
- Preventing Advanced Cyber Threats & Ransomware Attacks - Cybercriminals frequently target financial institutions with man-in-the-middle (MITM) attacks, ransomware, and phishing campaigns. Encrypted communication ensures that financial firms can securely exchange data, reducing the risk of cyber extortion and operational disruptions.
Encrypted Communication in Legal and Consultancy
Law firms, legal departments, and consultancy firms handle highly sensitive and confidential client information, including legal contracts, corporate strategies, intellectual property, and personal data. The legal industry is increasingly targeted by cybercriminals due to the value of the data they manage. A data breach not only compromises client trust but can also lead to financial losses, regulatory penalties, and reputational damage. Encryption plays a crucial role in ensuring secure communication, protecting attorney-client privilege, and safeguarding sensitive case materials.
Why Encryption is Essential for Legal and Consultancy Companies
- Protecting Attorney-Client Privilege & Confidentiality - Legal professionals are bound by strict confidentiality obligations, and any unauthorized access to client communications can compromise cases and violate legal ethics. Encryption ensures that sensitive legal discussions, case strategies, and evidence remain protected from unauthorized access.
- Preventing Cyber Espionage & Data Breaches - Law firms and consultancy firms deal with mergers and acquisitions, intellectual property disputes, and corporate litigation, all attractive targets for cyber espionage. Hackers, competitors, and even nation-state actors may attempt to intercept confidential legal strategies.
- Securing Cloud-Based Legal Collaboration & Remote Work - With the rise of digital transformation in the legal sector, many law firms and consultants store case files, contracts, and communications in cloud-based platforms. Without proper encryption, this data is vulnerable to unauthorized access and cyberattacks.
- Compliance with Data Protection & Legal Regulations - Legal and consultancy firms must comply with stringent data privacy laws to ensure that client data remains protected. Encryption is often a mandatory requirement under regulations such as:
- GDPR (General Data Protection Regulation - EU) - Requires encryption for client data stored and transmitted by legal firms.
- ABA (American Bar Association) Cybersecurity Guidelines - Recommends law firms implement encryption to protect client confidentiality.
- CCPA (California Consumer Privacy Act) - Mandates strong data protection measures, including encryption, to prevent data breaches.
- Preventing Insider Threats & Unauthorized Access - Law firms and consultancy firms often work with multiple stakeholders, including external legal experts, clients, and regulatory bodies. Without encryption, internal employees or third-party vendors with access to legal files could leak or misuse confidential information.
- Securing Legal Communications & Digital Evidence - Legal professionals communicate sensitive case details through emails, instant messaging, and video conferencing. Without encryption, confidential discussions can be intercepted, manipulated, or used as evidence against clients.
Encrypted Communication in Corporate
Corporations handle vast amounts of sensitive information, including intellectual property (IP), trade secrets, financial reports, strategic plans, and confidential customer data. Without proper encryption, businesses are at risk of corporate espionage, data breaches, and financial fraud. Encryption ensures that critical business communications remain confidential, secure, and protected from both internal and external threats.
Why Encryption is Essential for Corporations
- Protecting Intellectual Property & Trade Secrets - Intellectual property is one of the most valuable assets for corporations, especially in industries like technology, pharmaceuticals, and manufacturing. Competitors, cybercriminals, and even nation-state actors target corporate IP for financial gain or competitive advantage.
- Preventing Corporate Espionage & Insider Threats - Insider threats, whether intentional or accidental, pose a significant risk to businesses. Employees, contractors, or business partners with access to sensitive data can leak information, either for financial incentives or due to negligence. Encryption ensures that even if data is accessed, it remains unreadable without proper authorization.
- Securing Financial Transactions & Mergers & Acquisitions (M&A) - Large corporations frequently conduct multi-million-dollar transactions, mergers, and acquisitions that require absolute confidentiality. Hackers often target financial departments to intercept sensitive deal information and exploit market conditions.
- Preventing Phishing Attacks & CEO Fraud - Phishing remains one of the biggest cybersecurity threats in corporate environments. Cybercriminals impersonate executives, tricking employees into revealing confidential information or authorizing fraudulent transactions. Encrypted communication platforms ensure that corporate emails and messages are authenticated, reducing the risk of phishing attacks.
- Compliance with Data Protection & Industry Regulations - Corporations must comply with global data protection regulations to avoid legal repercussions and financial penalties. Encryption is a key requirement in compliance frameworks, ensuring that sensitive corporate data remains secure.
- GDPR (General Data Protection Regulation - EU) - Mandates encryption for protecting customer and employee data.
- SOX (Sarbanes-Oxley Act - US) - Requires encryption for financial records to prevent fraud.
- NIS2 (EU Network and Information Security Directive) - Enforces stricter encryption requirements for critical infrastructure industries.
- Enabling Secure Remote Work & Global Collaboration - With the rise of remote work and global teams, corporate communication has shifted to cloud-based platforms, video conferencing, and messaging apps. Unencrypted communications over public networks expose businesses to cyber risks. Encryption ensures secure collaboration while maintaining business continuity.
- Protecting Research & Development (R&D) Data - Companies investing in R&D, particularly in biotech, AI, and advanced technologies, are prime targets for cyber espionage. Encryption secures proprietary data, preventing competitors and foreign entities from stealing groundbreaking innovations.
Encrypted Communication for Frontline Teams
Frontline teams, such as healthcare professionals, emergency responders, and public safety officials, operate in high-stakes environments where secure, real-time communication is critical. These teams handle sensitive data, coordinate urgent responses, and make split-second decisions that impact lives. Without encrypted communication, they risk cyberattacks, data breaches, and operational disruptions that could compromise patient privacy, emergency response effectiveness, and national security.
Why Encryption is Essential for Frontline Teams
- Securing Patient Data in Healthcare - Medical institutions store and transmit vast amounts of confidential patient information, including electronic health records (EHRs), diagnostic reports, and treatment plans. Cybercriminals target healthcare systems due to the high value of medical data on the black market. Encryption ensures that sensitive patient records remain protected, even if systems are breached.
- Enabling Secure Public Safety Communications - Police, fire departments, and emergency teams rely on encrypted communication to securely share mission-critical information. Whether responding to a crisis, coordinating disaster relief, or managing large-scale events, public safety teams must ensure their communications are protected from eavesdropping and cyber threats.
- Protecting Emergency Response Coordination - During natural disasters, terrorist attacks, or pandemics, emergency response teams must coordinate efforts across agencies and geographies. Secure, encrypted communication is crucial to prevent disinformation, cyber disruptions, and unauthorized access to critical response plans.
- Compliance with Privacy & Security Regulations - Frontline teams must comply with stringent data protection laws to ensure the security of sensitive information. Encryption plays a vital role in meeting compliance requirements:
- HIPAA (Health Insurance Portability and Accountability Act - US) - Requires encryption of electronic health records to protect patient privacy.
- CJIS (Criminal Justice Information Services - US) - Mandates encryption for law enforcement data to prevent unauthorized access.
- NIS2 (EU Network and Information Security Directive) - Enforces encryption for critical infrastructure sectors, including emergency response services.
Encrypted communication is a lifeline for frontline teams, ensuring the confidentiality, integrity, and availability of critical information. From securing patient data in hospitals to protecting emergency response coordination, encryption is a non-negotiable element of modern frontline operations.
Chapter 3: Overcoming Challenges in Encrypted Communication
Common Misconceptions About Encrypted Communication
Encryption is often misunderstood, leading to resistance from decision-makers and employees alike. These misconceptions can delay implementation, weaken security strategies, and leave organizations vulnerable to cyber threats. Let’s break down some of the most common myths:
Myth 1: "Encryption Is Too Complex to Implement"
Many believe encryption requires advanced technical expertise, making it too complicated for non-technical users.
Reality: Modern encryption solutions are designed for seamless integration and ease of use. Secure messaging platforms, encrypted email services, and file protection tools now come with user-friendly interfaces and automated encryption protocols.
Myth 2: "Encryption Slows Down Performance"
Some organizations hesitate to use encryption due to concerns about latency, lag, or delays in communication and data processing.
Reality: With modern computing power and optimized encryption algorithms, performance impact is minimal. Many solutions use hardware acceleration (e.g., AES-NI) to encrypt data in real time without noticeable delays.
Myth 3: "Encryption Is Only for Large Enterprises"
Small and medium-sized businesses (SMBs) often assume that encryption is a luxury only big corporations need.
Reality: Cybercriminals frequently target SMBs due to weaker security, making encryption even more critical. Affordable, scalable encryption solutions allow businesses of all sizes to protect their sensitive data.
Myth 4: "Encryption Is Too Expensive"
Many governments and businesses worry that encryption solutions come with high costs for software, implementation, and maintenance.
Reality: The cost of encryption is far lower than the cost of a data breach. Regulatory fines, legal consequences, and reputational damage from unprotected data can be devastating.
Myth 5: "End-to-End Encryption Prevents Lawful Access"
Some governments and organizations fear that E2EE makes it impossible to detect criminal activities.
Reality: Encryption protects law-abiding users from cybercriminals, not the other way around. Governments and organizations can still monitor metadata and apply lawful access mechanisms within compliance frameworks without weakening encryption for everyone.
Balancing Security and Usability
One of the biggest challenges with encryption is striking the right balance between security and usability. If encryption tools are too complex, employees may bypass them, resorting to unsecured alternatives like personal messaging apps or unencrypted email.
To make encryption both secure and user-friendly, organizations must consider the following key factors:
Choosing Encryption Solutions with Seamless User Experience
- Zero-Click Encryption: The best encryption tools encrypt data automatically without requiring extra steps from the user.
- Single Sign-On (SSO) Integration: Reduces the number of passwords employees need to remember while maintaining security.
- Minimal Performance Impact: Optimized encryption should not slow down communication or data processing.
Making Encryption Intuitive for Employees
- Clear Guidelines on Secure Communication: Employees should know when to use encrypted messaging, emails, and file-sharing.
- Mobile-Friendly Encryption: Given the rise of remote work, encryption must work seamlessly across mobile devices without requiring extra configurations.
- Built-In Encryption for Collaboration Tools: Secure communication should be embedded within team collaboration platforms rather than requiring external applications.
Addressing Resistance to Encryption
- Security Training with Real-World Examples: Employees should understand why encryption is necessary and how it protects their work.
- Eliminating Unencrypted Alternatives: Organizations should disable non-secure communication methods (e.g., personal emails for work).
- Regular Security Audits & Feedback Loops: Collect employee feedback to ensure encryption solutions are effective without being disruptive.
Chapter 4: The Cost of Encryption: Is It Worth It?
Encryption is often viewed as an essential security measure, but businesses and governments must consider its financial and operational costs. From infrastructure investments to performance trade-offs, governments and organizations need to assess whether these costs justify the long-term benefits.
Breaking Down the Costs
The primary expenses of implementing encryption include:
- Technology Investments – Secure encryption solutions, such as end-to-end encryption (E2EE), hardware security modules (HSMs), and key management systems.
- Operational Overhead – Increased computational demands, potential performance slowdowns, and integration with existing systems.
- Compliance & Legal Costs – Ensuring encryption aligns with regulations such as GDPR, NIS2, and ISO 27001.
- Training & Expertise – IT teams require ongoing education to manage encryption strategies effectively.
The ROI of Encryption in Preventing Data Breaches
The financial impact of a data breach can be devastating, with costs including regulatory fines, legal fees, reputational damage, and operational downtime. Encryption significantly reduces these risks. Even if encrypted data is stolen, it remains unreadable without decryption keys, preventing costly legal and compliance repercussions. Additionally, encryption strengthens Zero Trust security models, reducing insider threats and unauthorized access.
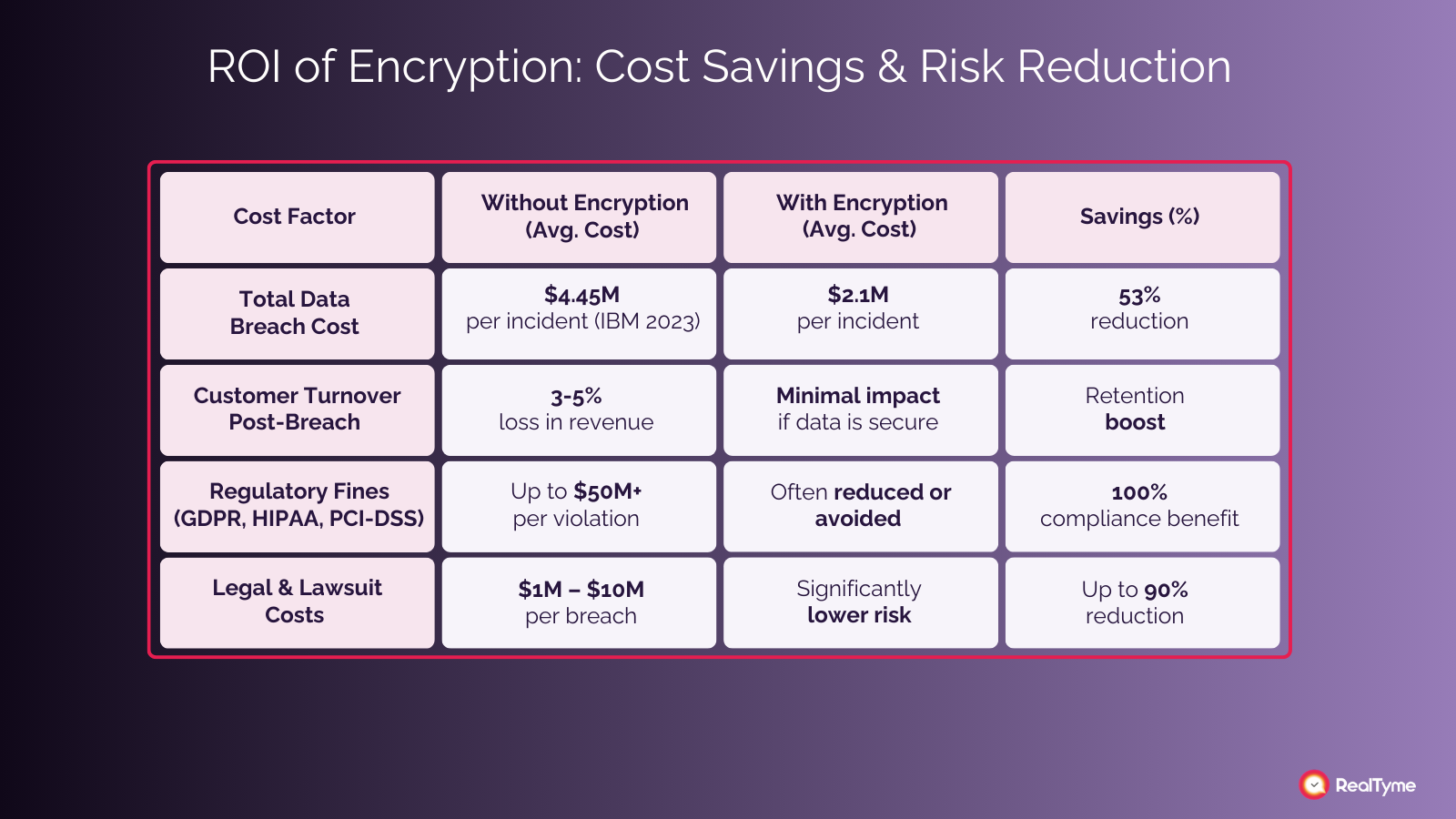
Optimizing Encryption Budgets
Governments and organizations can minimize encryption costs while maximizing protection by:
- Prioritizing Critical Data – Encrypting only the most sensitive information to balance security and performance.
- Leveraging Efficient Algorithms – Implementing optimized encryption methods like AES-256 and elliptic curve cryptography to reduce processing overhead.
- Using Hybrid Approaches – Combining on-premises and cloud-based encryption solutions for flexibility.
- Automating Key Management – Investing in automated tools to prevent costly human errors in encryption key handling.
Ultimately, the cost of encryption pales in comparison to the financial and reputational losses from a security breach. When implemented strategically, encryption is not just an expense but an investment in resilience and long-term security.
Key Features to Look for in Encrypted Communication Platform
When evaluating an encrypted communication platform, these key features are essential for ensuring robust security and seamless usability:

1. Strong Cryptography
When evaluating a secure communication platform, the strength and security of its cryptographic foundation are paramount. A well-designed platform must incorporate multiple layers of protection to ensure confidentiality, integrity, and authentication, safeguarding sensitive data from evolving cyber threats. Below are the key factors that determine the robustness of an encrypted communication solution:
- Robust End-to-End Encryption (E2EE) Protocols
A secure communication platform must implement strong, well-vetted E2EE protocols to prevent unauthorized access to data in transit. This means that messages, calls, and files are encrypted on the sender’s device and can only be decrypted by the intended recipient—ensuring that even the service provider cannot access the content. A reliable E2EE implementation relies on authenticated key exchange mechanisms, secure key distribution, and resistance against cryptographic attacks.
- Strong Mutual Authentication
Secure communication is not just about encryption but also about verifying the identity of all parties involved. Mutual authentication ensures that both the sender and recipient are who they claim to be, preventing man-in-the-middle (MITM) attacks and impersonation. This is typically achieved using certificate-based authentication, Zero-Knowledge Proofs (ZKP), or secure public-key infrastructures (PKI).
- State-of-the-Art Cipher Suites with Aligned Key Lengths
The security of an encryption system heavily depends on the choice of cipher suites and the alignment of key lengths with current cryptographic best practices. The platform should support:
- Advanced Encryption Standard (AES-256) for symmetric encryption to ensure high-speed, secure data protection.
- Elliptic Curve Cryptography (ECC)with 384-bit or higher key sizes, offering equivalent security to traditional RSA but with better efficiency.
- ChaCha20-Poly1305 as an alternative for environments where hardware acceleration for AES is unavailable.
- Secure hash functions like SHA-3 for ensuring data integrity. Selecting cryptographic primitives with appropriate key lengths ensures resilience against brute-force attacks while maintaining optimal performance.
- Post-Quantum Cryptography (PQC) Transition Roadmap with Crypto Agility
As quantum computing advances, traditional cryptographic algorithms like RSA, ECC, and Diffie-Hellman are at risk of being broken. A future-proof encryption platform should have a PQC transition strategy in place, ensuring readiness for quantum-resistant algorithms. This includes:
- Supporting NIST-recommended post-quantum algorithms like Kyber (for key exchange) and Dilithium (for digital signatures)
- Implementing hybrid cryptographic approaches, combining classical encryption with PQC to maintain backward compatibility.
- Ensuring crypto agility, allowing the system to seamlessly update and transition to stronger cryptographic methods as new standards emerge.
2. Zero-Knowledge Architecture
Zero-knowledge architecture is a privacy-first feature that ensures the platform’s service provider does not have access to the user’s data. This is one of the most important considerations when selecting an encrypted communication tool, as it guarantees that sensitive data is entirely in the hands of the user, protected from potential data breaches or misuse by the service provider.
A zero-knowledge system means that even the platform provider cannot read or decrypt user data, as the encryption keys are stored only on the user’s device. This is especially critical for users dealing with highly sensitive information, such as legal teams, healthcare providers, or government organizations. Zero-knowledge architecture provides an additional layer of privacy, ensuring that data remains private even if the platform itself is compromised.
3. Fully Open-Source vs. Hybrid Solutions
Another critical consideration is whether to opt for a fully open-source or hybrid encrypted communication solution, each with its own advantages and trade-offs.
Fully open-source solutions provide complete transparency, allowing users to review, modify, and audit the entire codebase. This openness fosters community-driven development, where vulnerabilities are often detected and patched quickly. However, these solutions may require technical expertise for secure configuration and ongoing management, and they often lack dedicated support.
Hybrid solutions, on the other hand, combine various open-source components with proprietary enhancements. These platforms are typically backed by a dedicated company that ensures optimal user experience, provides professional support, and integrates advanced security features. While hybrid solutions offer a more polished and user-friendly experience, they may involve licensing costs and require trust in the vendor to manage security and privacy.
Choosing between open-source and hybrid solutions requires balancing the need for transparency, control, and customization against the demand for reliability, ease of use, and professional support.
4. Usability and Cross-Platform Compatibility
While encryption is essential, usability cannot be overlooked. The platform should be user-friendly and intuitive, allowing both technical and non-technical users to communicate securely without unnecessary complexity. A complicated user interface can hinder adoption and cause friction within organizations.
Cross-platform compatibility is also crucial, especially for teams and organizations that use a variety of devices and operating systems. Ensure that the platform works seamlessly across desktop, mobile, and tablet devices and supports all major operating systems like Windows, macOS, iOS, and Android. This ensures that users can securely communicate from anywhere, whether in the office, at home, or on the go.
When selecting an encrypted communication platform, it’s crucial to evaluate the features that will best protect your organization’s sensitive data. The right platform should not only offer robust security measures but also integrate seamlessly into your existing systems while being user-friendly.
With cyber threats evolving rapidly, choosing a platform with the right encryption protocols, privacy features, and compatibility is more important than ever. And this is where RealTyme differentiates itself. While many platforms integrate encryption as an optional layer, RealTyme is built with end-to-end encryption (E2EE) by default, securing every message, call, video conference, and file transfer without requiring manual activation. For organizations handling sensitive communications, whether in legal, healthcare, government, or defense, this level of seamless, always-on encryption eliminates risks tied to human error and ensures uncompromising privacy across all channels.
5. Deployment Flexibility
Organizations have varying security and compliance needs, making deployment flexibility crucial. The platform should support cloud, on-premises, and hybrid deployment models, along with self-hosting and sovereign cloud options, ensuring control over data storage and encryption policies.
How to Select the Best Encrypted Communication Platform
By now, you understand the importance of encryption in safeguarding your communications, but with so many options available, how do you determine which platform truly meets your security and privacy needs?
To make the right choice, it's crucial to look beyond basic encryption and evaluate the key factors that ensure uncompromised protection. Here’s what to consider when selecting the best encrypted communication platform like RealTyme:
1. Cost
The budget available for implementing an encrypted communication system is often one of the most important factors in decision-making. While open-source solutions may be free, they often require more customization and technical expertise, while proprietary platforms may come with licensing fees or subscription costs. Businesses must weigh the costs against the platform's features, level of security, and the potential risks of inadequate encryption.
RealTyme, for example, offers transparent pricing and tailored plans with no hidden fees, providing a balance between enterprise-grade security and long-term affordability. Unlike open-source platforms that require ongoing maintenance, RealTyme delivers an out-of-the-box, fully encrypted communication system by eliminating the need for costly security add-ons or IT overhead.
2. Scalability
As governments and organizations grow, their encryption needs will likely evolve. It's essential to choose a platform that can scale to meet the demands of a growing user base or increased data volume.
Built to grow with your organization, RealTyme supports seamless scalability without compromising security or performance. Whether adding a few users or scaling up to thousands, RealTyme maintains the same high level of security and privacy, making it ideal for dynamic and growing teams.
3. Compliance with Industry Regulations
Every industry has its own set of regulatory requirements for data protection, and selecting a platform that ensures compliance with these laws is critical. Whether it’s GDPR for organizations operating in the EU, HIPAA for healthcare, or PCI-DSS for financial institutions, ensure that the platform meets the specific compliance standards relevant to your industry.
With built-in data sovereignty controls and privacy-focused encryption policies, RealTyme ensures your organization can meet compliance requirements without worrying about unauthorized access or regulatory violations.
4. Security Requirements
The level of security required will depend on the type of data you are transmitting. For highly sensitive data, such as classified government information or confidential medical records, you may require the highest levels of encryption (AES-256, ECC, and Quantum-Safe encryption). For less sensitive data, a lower level of security might suffice.
Choose a platform that aligns with your organization’s specific security needs. RealTyme enforces end-to-end encryption (E2EE) by default, utilizing AES-256 encryption with strong mutual authentication, and quantum-safe cryptography in the short-term to future-proof communications against emerging threats.
Selecting the right encrypted communication platform requires a careful evaluation of your organization’s requirements, including security, compliance, cost, and scalability. The right platform will offer a combination of robust encryption, ease of use, and features tailored to your specific operational needs. And by choosing RealTyme, you don’t have to compromise between security, scalability, and compliance. It delivers a holistic, privacy-first solution, ensuring seamless collaboration without sacrificing control over your sensitive communications.
Chapter 6: Implementing Encrypted Communication in Your Organization
Encryption is only effective when properly implemented, managed, and enforced across an organization. Simply adopting encrypted communication tools is not enough. Employees must be trained, policies must be enforced, and insider threats must be mitigated.
Implementation & Architecture
Once you've selected a platform, the next step is ensuring that it’s implemented effectively and securely within your organization. The architecture of the encrypted communication system plays a critical role in how secure and scalable the platform will be. Key management, secure protocols, and hardware integration are all integral to ensuring that sensitive data remains protected at all times. Additionally, the decision of whether to deploy encryption on-premises or in the cloud impacts both security and usability.
1. Key Management & Public Key Infrastructure (PKI)
Key management is a critical component of any encrypted communication system. It involves the generation, storage, distribution, and revocation of encryption keys. PKI is a framework that manages digital keys and certificates, ensuring secure communication and transaction validation. PKI is essential for ensuring that encryption keys are securely stored and that only authorized users can access or exchange them. A well-implemented PKI system offers the ability to authenticate users, encrypt data, and maintain data integrity.
2. Hardware Security Modules (HSMs)
HSMs are physical devices used to store cryptographic keys securely. These devices are tamper-resistant and designed to prevent unauthorized access to sensitive data. HSMs are often used in conjunction with PKI to add an additional layer of physical security for encryption keys, ensuring that they cannot be compromised or accessed even in the event of a physical breach. HSMs are particularly important for organizations that require extremely high security, such as government agencies, financial institutions, and healthcare providers.
3. Secure Protocols
The encryption platform should support a variety of secure communication protocols to ensure that data remains protected across different channels.
- TLS (Transport Layer Security): This protocol secures data transmitted over the internet, such as during browsing or sending emails. It encrypts the communication between a user’s device and the server, preventing man-in-the-middle attacks.
- IPsec (Internet Protocol Security): IPsec secures IP communications by authenticating and encrypting each data packet in a communication session. It is widely used for securing Virtual Private Networks (VPNs) and ensuring that all data transferred over the internet remains confidential.
- E2EE Messaging Protocols: These protocols are used by applications like WhatsApp and Signal to provide end-to-end encryption for text, voice, and video communications.
4. On-Premises vs. Cloud Deployment
When choosing an encrypted communication platform, governments and organizations must decide whether they prefer a full self-hosted on-premises solution (where backend servers and data are kept within their own infrastructure) or a cloud-based solution (where hosting and storage are handled by a third-party service provider).
- On-Premises Deployment: This solution offers the highest level of control over the infrastructure, allowing organizations to maintain complete ownership and security of their data. However, it can be costly to maintain and requires in-house expertise to manage and configure securely.
- Cloud Deployment: Cloud-based platforms are often easier to implement and manage, offering the benefit of scalability and lower upfront costs. Organizations can choose a private cloud, which provides dedicated infrastructure that is partially managed by a third party, or a public cloud, which offers cost efficiency and flexibility but relies almost fully on third-party providers for data protection. Sensitive data may be better suited for private cloud, while public cloud solutions can be ideal for organizations prioritizing ease of deployment and cost savings.
Setting Up Secure Messaging and Group Calls
Organizations rely on communication tools for everyday operations, whether it's internal messaging, conference calls, or file sharing. However, without encryption, these interactions become prime targets for cybercriminals, competitors engaging in corporate espionage, and even state-sponsored attackers. Selecting the right encrypted communication platform requires evaluating multiple factors:
- End-to-End Encryption (E2EE) – Ensures that messages, calls, and shared files are encrypted on the sender's device and only decrypted on the recipient's device, preventing unauthorized access at any point in transit.
- Zero-Trust Security Model – Access to sensitive communications should be restricted based on authentication protocols, ensuring that even internal IT teams cannot access encrypted data.
- Metadata Protection – Some encryption tools encrypt message content but still expose metadata (e.g., who is communicating with whom). Advanced solutions prevent even metadata leaks.
- Regulatory Compliance – Depending on the industry, solutions should comply with standards such as GDPR, HIPAA, or NIS2.
- Deployment Options (On-Premises vs. Cloud) – Highly sensitive organizations may prefer on-premises encryption solutions for greater control.
Training Employees on Secure Communication Practices
Even the most advanced encryption tools can fail if employees misuse them, fall victim to phishing attacks, or unknowingly expose sensitive information. For encryption to be truly effective, organizations must prioritize security training to ensure employees understand:
- How to use encrypted communication tools correctly;
- The risks of cyber threats, such as phishing and social engineering;
- The importance of verifying the identity of communication recipients;
- Why sensitive conversations should never take place on unsecured channels.
Many employees may not fully understand what encryption does or why it is necessary. Training should start with real-world examples of security breaches that could have been prevented by proper encryption. Employees must be trained to:
- Verify senders before opening attachments or clicking links;
- Recognize warning signs of phishing attempts, such as urgent language and unusual requests;
- Report suspicious messages immediately to security teams.
Simulated phishing attacks should be conducted regularly to assess employee preparedness.
Encryption is effective only when used correctly. Employees should be trained on best practices, such as:
- Never forwarding encrypted messages to unapproved contacts;
- Ensuring encrypted calls are conducted in private, secure locations;
- Disabling automatic backups if they store unencrypted versions of messages.
Encryption should not be left to employee discretion; it must be a mandatory requirement enforced through corporate security policies. Without proper enforcement, employees may default to insecure communication methods, creating security gaps.
Insider Threats & Human Error
While external hackers pose a significant threat, insider threats, whether accidental or intentional, are equally dangerous. Employees or contractors with access to sensitive data can:
- Accidentally leak encrypted information by misconfiguring security settings;
- Intentionally steal sensitive data for financial or personal gain;
- Fall victim to social engineering attacks, exposing encryption keys or login credentials.
Encryption Compliance & Audits
Encryption is not just a cybersecurity best practice but a legal and regulatory requirement for governments and enterprises worldwide. Organizations must adhere to strict compliance frameworks and conduct regular encryption audits to ensure their security measures are robust and up to date. Failing to do so can lead to hefty fines, legal consequences, and reputational damage.
Regular encryption audits help organizations:
- Identify vulnerabilities in encryption protocols and key management;
- Ensure compliance with international and industry-specific regulations;
- Prevent costly penalties and legal repercussions for non-compliance;
- Strengthen cybersecurity defenses against evolving threats.
A well-executed encryption audit can prevent such incidents by ensuring compliance and identifying gaps before attackers do. As already explained in the above sections, different industries enforce specific encryption standards to protect sensitive data. Below are the most critical compliance frameworks:
1. National Security Laws & Data Sovereignty
Governments worldwide enforce national security laws requiring encryption to protect critical infrastructure, defense data, and citizen information.
- United States - Executive Order on Improving Cybersecurity (2021): Requires federal agencies and contractors to use strong encryption to protect sensitive government data.
- China’s Cybersecurity Law (CSL): Mandates encryption for data stored within China and restricts cross-border data transfers.
- Australia’s Telecommunications & Other Legislation Act (TOLA): Requires tech providers to implement encryption backdoors for government access (controversial).
- European Data Sovereignty Laws: Encourage the use of on-premises or EU-based encryption solutions to protect data from foreign surveillance.
How Encryption Ensures Compliance with National Security Laws:
- Military-Grade Encryption (AES-256, ECC, PQC) protects classified government data.
- Data Sovereignty Encryption ensures compliance by storing data in jurisdiction-approved locations.
- End-to-End Encrypted Messaging secures internal communications against foreign espionage.
The evolving landscape of national security laws underscores the critical role of encryption in protecting sensitive data and ensuring compliance with varying regional requirements. Governments continue to enforce these laws to bolster data protection and safeguard national interests.
2. NIST (National Institute of Standards and Technology) - U.S. Encryption Guidelines
NIST sets encryption and cybersecurity standards used by government agencies, contractors, and enterprises worldwide.
- FIPS 140-3 (Federal Information Processing Standard): Specifies approved encryption algorithms like AES-256, ECC, and RSA.
- NIST Special Publication 800-57: Defines best practices for cryptographic key management.
- NIST Special Publication 800-171: Requires encryption for handling controlled unclassified information (CUI) in government contracts.
NIST's encryption standards provide a crucial foundation for ensuring the security and integrity of sensitive data in government and private sector operations, helping to establish trust and reliability in digital communications.
3. ISO 27001 - Global Information Security Standard
ISO 27001 is an internationally recognized information security management system (ISMS) framework that mandates encryption for protecting data confidentiality, integrity, and availability.
- Control A.10.1: Encryption must be implemented to protect sensitive data.
- Risk-Based Approach: Organizations must conduct encryption risk assessments and document encryption policies.
- Regular Audits: Organizations must review encryption mechanisms to prevent vulnerabilities.
ISO 27001 emphasizes the importance of a comprehensive, risk-based approach to encryption, ensuring organizations remain proactive in safeguarding their sensitive information and maintaining trust with stakeholders.
4. GDPR (General Data Protection Regulation) - European Union
GDPR enforces strict data encryption requirements to protect personal and financial data of EU citizens.
- Article 32: Organizations must implement encryption as a security measure.
- Article 34: If encrypted data is breached, companies may not need to notify individuals, reducing liability.
- Fines for Non-Compliance: Up to €20 million or 4% of global annual turnover.
GDPR's encryption mandates highlight the need for stringent data protection measures in the EU, empowering organizations to secure personal data and minimize the impact of potential breaches while avoiding heavy penalties.
5. HIPAA (Health Insurance Portability and Accountability Act) - Healthcare
HIPAA mandates encryption for electronic Protected Health Information (ePHI) to ensure patient confidentiality.
- Data in Transit & At Rest Encryption: Required for patient data protection.
- Access Controls: Only authorized medical personnel can access data.
- Audit Logs: Track encrypted data access to detect anomalies.
HIPAA’s encryption requirements are pivotal in safeguarding patient data, ensuring that healthcare organizations maintain privacy, protect against unauthorized access, and comply with regulations for sensitive health information.
6. PCI-DSS (Payment Card Industry Data Security Standard) - Finance
PCI-DSS enforces strong encryption standards for securing credit card transactions and banking data.
- End-to-End Encryption (E2EE): Prevents credit card fraud.
- Tokenization: Replaces cardholder data with encrypted tokens.
- TLS/SSL Encryption: Secures online banking platforms.
PCI-DSS encryption standards are essential in protecting financial transactions and payment data, fortifying consumer trust and preventing data breaches in the finance sector.
Conducting Encryption Audits & Penetration Testing
Governments and organizations must regularly audit their encryption systems to identify weaknesses before attackers do. Encryption audits should include:
- Penetration Testing: Simulating cyberattacks to test encryption strength.
- Key Management Audits: Reviewing encryption key lifecycle policies.
- Compliance Gap Analysis: Checking adherence to GDPR, HIPAA, PCI-DSS, etc.
- Algorithm Strength Testing: Ensuring encryption algorithms meet industry standards.
Encryption Audit Checklist:
- Ensure AES-256, ECC and post-quantum cryptography is used.
- Conduct TLS certificate expiration checks.
- Implement automated encryption monitoring tools.
- Review access logs for unauthorized decryption attempts.
To remain compliant with global encryption regulations, governments and organizations should:
- Implement Zero Trust Encryption: Verify every access request before decrypting data.
- Use Quantum-Safe Cryptography: Future-proof against quantum attacks.
- Automate Compliance Audits: Deploy tools that continuously monitor encryption policies.
- Adopt End-to-End Encryption (E2EE): Secure internal and external communications.
- Regularly Rotate Encryption Keys: Prevent unauthorized access due to key compromise.
Chapter 7: Emerging Technologies in Encrypted Communication
New encryption methods are being developed to address future threats and enhance privacy. Here are some of the most promising innovations shaping the future of secure communication:

Quantum-Resistant Encryption
With quantum computing on the horizon, current encryption algorithms will eventually become obsolete. Quantum-resistant encryption, also known as post-quantum cryptography (PQC), is designed to withstand quantum attacks. Governments and enterprises must prepare for the post-quantum era by transitioning to quantum-safe cryptographic standards. The U.S. National Institute of Standards and Technology (NIST) is already finalizing post-quantum encryption algorithms, and organizations should start evaluating migration strategies now.
- Lattice-based cryptography – Uses complex mathematical structures to create encryption keys that quantum computers can’t easily break;
- Multivariate cryptography – Based on solving complex algebraic equations, making it resistant to quantum decryption methods;
- Hash-based cryptography – A highly secure approach using cryptographic hash functions instead of traditional key-based encryption.
As quantum computing advances, adopting quantum-resistant encryption becomes a critical step for securing sensitive data against future threats, ensuring long-term data protection in the post-quantum era. Governments and organizations must act now to integrate these emerging standards and safeguard against quantum-driven vulnerabilities.
AI-Powered Threat Detection
Artificial intelligence is being used both to attack and defend encrypted systems. AI-powered security solutions can:
- Detect anomalies in encrypted traffic to identify potential breaches;
- Predict new encryption-breaking techniques before attackers exploit them;
- Automate encryption key lifecycle management, reducing human error.
AI-powered threat detection is revolutionizing encrypted systems by proactively identifying potential security breaches and optimizing key management, offering a future-proof approach to counter increasingly sophisticated attacks. Embracing AI in encryption will provide a significant edge in staying ahead of evolving threats
Homomorphic Encryption: Computing on Encrypted Data
Homomorphic encryption allows computations to be performed on encrypted data without decrypting it, enabling privacy-preserving applications such as:
- Secure cloud computing – Businesses can analyze encrypted data in the cloud without exposing it to service providers;
- Privacy-preserving AI – Enables AI models to process sensitive medical or financial data without accessing raw information.
Homomorphic encryption promises a future where sensitive data remains secure while still being analyzed and processed, empowering industries like healthcare and finance to unlock insights without compromising privacy. This breakthrough offers transformative potential for privacy-preserving technologies across sectors.
Decentralized Identity and Blockchain Security
Blockchain-based encryption is transforming secure communication by eliminating central points of failure. Some key applications include:
- Self-sovereign identity (SSI) – Users control their encrypted identity data without relying on centralized authorities;
- Immutable encrypted storage – Blockchain ensures data integrity by preventing unauthorized alterations.
As data sovereignty becomes a growing concern, decentralized identity frameworks will reduce reliance on central databases, preventing large-scale breaches. Blockchain can further enhance zero-knowledge authentication, allowing users to prove identity without exposing personal data.
The Impact of Emerging Threats on Encrypted Communication
The cybersecurity landscape is evolving rapidly, and new threats are testing the resilience of encryption protocols. Some of the most pressing threats include:
AI-driven cyberattacks are increasingly sophisticated, using machine learning to enhance phishing, automate malware adaptation, and analyze encrypted traffic for vulnerabilities. While AI cannot yet break strong encryption, it accelerates brute-force attacks on weak passwords and outdated cryptographic methods. Defenders must counter this with AI-powered anomaly detection, strong authentication, and continuously updated encryption protocols to stay ahead of evolving threats.
- Advanced Ransomware & Data Extortion
Modern ransomware attacks no longer just encrypt files. They also exfiltrate data before encryption, allowing attackers to threaten leaks even if businesses refuse to pay. Stronger end-to-end encryption (E2EE) and secure key management can mitigate these risks.
- National State Attacks & Cyber Warfare
Governments worldwide are investing in offensive cybersecurity capabilities. State-sponsored attackers may target encryption backdoors, exploit weak cryptographic implementations, or even use quantum computing to break existing encryption. Organizations must stay compliant with evolving encryption regulations while maintaining secure architectures.
How Governments and Businesses Can Stay Ahead
Encryption is not a one-time solution, but it requires continuous adaptation to counter new threats. Here’s how your organization can stay ahead:
1. Regularly Update Encryption Standards
- Adopt post-quantum cryptographic algorithms as they become available;
- Transition to quantum-resistant encryption before quantum threats emerge.
2. Invest in Cybersecurity Training & Awareness
- Educate employees on secure encryption practices to reduce human errors;
- Train IT teams on emerging cryptographic technologies like homomorphic encryption and blockchain security.
3. Monitor Emerging Threats & Regulations
- Stay updated on NIST’s post-quantum cryptography recommendations;
- Monitor government regulations on encryption (e.g., GDPR, NIS2, U.S. federal encryption standards).
4. Strengthen Key Management & Zero Trust Security
- Implement automated key rotation and hardware security modules (HSMs) for key storage;
- Enforce a Zero Trust security model, ensuring encryption is layered across networks, endpoints, and communications.
5. Explore Decentralized Solutions
- Use blockchain-based solutions for identity protection;
- Implement zero-knowledge proof authentication for privacy-preserving verification.
Conclusion
And there you have it! We’ve explored the key points from the fundamentals of encrypted communication to choosing the right solutions and futureproofing against emerging threats. Whether you're focused on securing sensitive government data, protecting corporate assets, or ensuring compliance with industry regulations, one thing is clear: encryption is no longer optional, it’s essential.
If you're ready to take your organization’s security to the next level with a communication solution that prioritizes privacy, compliance, and future-proof encryption, we’re here to help. Let’s discuss how RealTyme can empower your team with end-to-end encryption and privacy-first technology. Contact us today to start your journey toward truly secure communication.









.png)
